A bank has three types of accounts: checking, savings, and loan. Following are the attributes for each type of account:
CHECKING: Acct No, Date Opened, Balance, Service Charge
SAVINGS: Acct No, Date Opened, Balance, Interest Rate
LOAN: Acct No, Date Opened, Balance, Interest Rate, Payment
Assume that each bank account must be a member of exactly one of these subtypes. Using generalization, develop an EER model segment to represent this situation using the traditional EER notation, the Visio notation, or other tools like Lucidchart / Draw.io. Remember to include a subtype discriminator.
Answers
Answer:
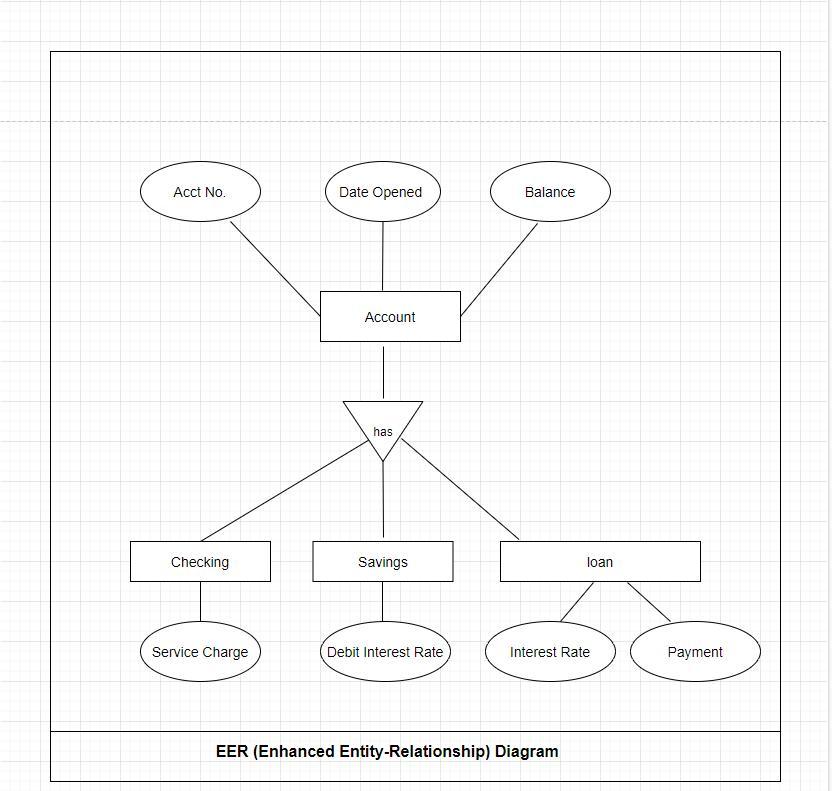
please find the attachment of a graph:
Explanation:
Description of the model:
Generalization is the method used here just for the EER model, which sweeping generalization is a way to identify the common characteristics of a sequence to create a common entity. This is an approach from the bottom up. Its verification, savings, and credit firms are extended to a higher-level object's account. So, the entity entities (Account) are the common traits of these bodies. As well as the specific qualities are the part of specialized entities (checks, savings, and loans). This EER model is shown via the subgroup and supertype notes. The Balance has calculated the distance, throughout the entity type entity are key patterns of the subgroup entities. The wood beaded includes Acct No, Balanced and Open Date. The key was its underliner Acct No. the very first key. CHECKING, SAVINGS, and LOAN are the subsection organizations of the Supertype Account.Its subtypes get the traits that are not normal. It Testing feature is the uncommon extra fee feature. Its SAVINGS post-type feature has the peculiar exchange rate feature. Its LOAN subgroup feature produces unusual interest in fixed payment characteristics.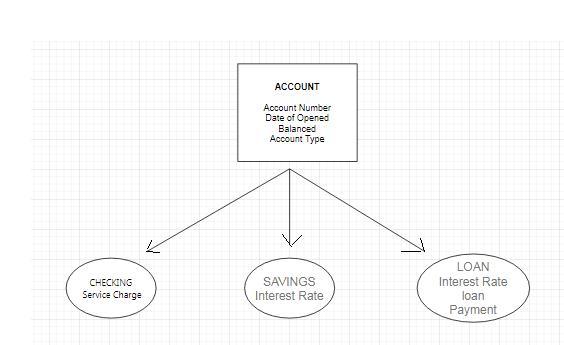
Enhanced Entity relationships[EER] represent the requirements and complexities of a complex database.
What is Enhanced Entity-relationship?Here, the account entity generalized into three entities and these are checking, savings, and loan.
Also, the common attribute the three of them have can be considered in the account entity which is common in them while the individual attributes must be specified under its own entity.
EER models are the helpful tools used for designing databases that have high-level models.
Learn more about databases on:
https://brainly.com/question/518894
Related Questions
Which is an example of a function header in Python? left (40): def drawT(): left def
Answers
Answer:
B
Explanation:
Answer:
b def drawT():
Explanation:
In HTML5, the
(line break) tag does not require a closing tag.
true or false
Answers
"Jean-luc Doumont notes that slide software is an effective presentation tool, especially when the speech goal is to:"
Answers
Hi, your question is incomplete. Here are the options:
A. persuade the audience.
B, encourage critical thinking.
C. increase discussion.
D. relay detailed information
Answer:
D. relay detailed information
Explanation:
Indeed, slide software (like MS Powerpoint) would be an effective presentation tool, especially when the speech goal is to relay detailed information.
For example, a graph showing the exponential growth in the number of smartphone users in the United States for the last 15 years would be effectively presented using a slide that shows this data because it will allow the audience to easily see the detailed information.
Write a program whose inputs are three integers, and whose output is the smallest of the three values. Use else-if selection and comparative operators such as '<=' or '>=' to evaluate the number that is the smallest value. If one or more values are the same and the lowest value your program should be able to report the lowest value correctly. Don't forget to first scanf in the users input.
Ex: If the input is: 7 15 3
the output is: 3
You should sketch out a simple flowchart to help you understand the conditions and the evaluations needed to determine what number is the correct answer. This type of tool can help determine flaws in a logical design.
Answers
Answer:
The Program written in C is as follows:
#include <stdio.h>
int main() {
int num1, num2, num3, smallest;
printf("Enter any three numbers: ");
scanf("%d", &num1); scanf("%d", &num2); scanf("%d", &num3);
if(num1 <= num2 && num1 <= num3) {
smallest = num1;
}
else if(num2 <= num1 && num2 <= num3) {
smallest = num2;
}
else {
smallest = num3;
}
printf("Smallest: ");
printf("%d", num3);
return 0;
}
Explanation:
This line declares necessary variables
int num1, num2, num3, smallest;
This line prompts user for input of three numbers
printf("Enter any three numbers: ");
This lines get input for the three numbers
scanf("%d", &num1); scanf("%d", &num2); scanf("%d", &num3);
The following if/else statements determine the smallest of num1, num2 and num3 and assigns to variable smallest, afterwards
if(num1 <= num2 && num1 <= num3) {
smallest = num1;
}
else if(num2 <= num1 && num2 <= num3) {
smallest = num2;
}
else {
smallest = num3;
}
The next two lines print the smallest value
printf("Smallest: ");
printf("%d", num3);
(1) Prompt the user to enter a string of their choosing. Output the string.
Ex: Enter a sentence or phrase: The only thing we have to fear is fear itself. You entered: The only thing we have to fear is fear itself.
(2) Complete the GetNumOfCharacters() function, which returns the number of characters in the user's string. Use a for loop in this function for practice. (2 pts)
(3) In main(), call the GetNumOfCharacters() function and then output the returned result. (1 pt) (4) Implement the OutputWithoutWhitespace() function. OutputWithoutWhitespace() outputs the string's characters except for whitespace (spaces, tabs). Note: A tab is '\t'. Call the OutputWithoutWhitespace() function in main(). (2 pts)
Ex: Enter a sentence or phrase: The only thing we have to fear is fear itself. You entered: The only thing we have to fear is fear itself. Number of characters: 46 String with no whitespace: The only thing we have to fear is fear itself.
Answers
Answer:
See solution below
See comments for explanations
Explanation:
import java.util.*;
class Main {
public static void main(String[] args) {
//PrompT the User to enter a String
System.out.println("Enter a sentence or phrase: ");
//Receiving the string entered with the Scanner Object
Scanner input = new Scanner (System.in);
String string_input = input.nextLine();
//Print out string entered by user
System.out.println("You entered: "+string_input);
//Call the first method (GetNumOfCharacters)
System.out.println("Number of characters: "+ GetNumOfCharacters(string_input));
//Call the second method (OutputWithoutWhitespace)
System.out.println("String with no whitespace: "+OutputWithoutWhitespace(string_input));
}
//Create the method GetNumOfCharacters
public static int GetNumOfCharacters (String word) {
//Variable to hold number of characters
int noOfCharactersCount = 0;
//Use a for loop to iterate the entire string
for(int i = 0; i< word.length(); i++){
//Increase th number of characters each time
noOfCharactersCount++;
}
return noOfCharactersCount;
}
//Creating the OutputWithoutWhitespace() method
//This method will remove all tabs and spaces from the original string
public static String OutputWithoutWhitespace(String word){
//Use the replaceAll all method of strings to replace all whitespaces
String stringWithoutWhiteSpace = word.replaceAll(" ","");
return stringWithoutWhiteSpace;
}
}
Which of the following behaviors is considered ethical?
copying another user’s password without permission
hacking software to test and improve its efficiency
using a limited access public computer to watch movies
deleting other user’s files from a public computer
Answers
Answer:
using a limited access public computer to watch movies
Explanation:
Cause it doesn't involve you performing any illegal actions.
Answer:
C. using a limited access public computer to watch movies
Explanation:
IM A DIFFERENT BREEED!!
PLUS NOTHING ELSE MAKES SENSE LOL!
best answer brainliest :)
ridiculous answers just for points will be reported
thank you! Most jobs in information technology require expertise in _____.
most of the layers
all of the layers
one layer
a couple of the layers
Answers
Answer:
all of the layers
Explanation:
Answer:
a couple of the layers
Explanation: says it in the first sentence in the last paragraph of this image
40 POINTS IF YOu ANSWER FOR EACH STEP.
When your friend DaJuan turns on his computer, he hears four beeps. The computer won’t fully boot. DaJuan has a Dell computer with a quad core processor and has recently upgraded his RAM.
Apply the troubleshooting methodology to help DaJuan understand and resolve his problem. The steps of the methodology are listed for you. Copy them into a document and use them to write suggestions for DaJuan at each step.
1.Identify the Problem
2.Internet Research
3.Establish a Theory of Probable Cause
4.Test the Theory
5.Establish a Plan of Action
6.Implement the Solution or Escalate
7.Verify Full System Functionality
8.Document Findings.
Answers
Answer:
4 beeps indicate a Memory Read / Write failure. Try re-seating the Memory module by removing and reinserting it in the slot. This could mean it could've just jiggled loose after a while or dust, there could be a hundred other problems but those are the two most common.n
Explanation:
Match letters from column B to Column A by looking at the picture above.
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
This question is about mapping correct terms with their number in the given picture. The correct matching of Column A and Column B is given below
Column A Column B
Horizontal axis 3
Legend 4
Vertical axis 2
Chart Data 1
What does GDF is a measure of a nations?
Answers
Find the maximum value and minimum value in milesTracker. Assign the maximum value to maxMiles, and the minimum value to minMiles. Sample output for the given program:
Min miles: -10
Max miles: 40
Here's what I have so far:
import java.util.Scanner;
public class ArraysKeyValue {
public static void main (String [] args) {
final int NUM_ROWS = 2;
final int NUM_COLS = 2;
int [][] milesTracker = new int[NUM_ROWS][NUM_COLS];
int i = 0;
int j = 0;
int maxMiles = 0; // Assign with first element in milesTracker before loop
int minMiles = 0; // Assign with first element in milesTracker before loop
milesTracker[0][0] = -10;
milesTracker[0][1] = 20;
milesTracker[1][0] = 30;
milesTracker[1][1] = 40;
//edit from here
for(i = 0; i < NUM_ROWS; ++i){
for(j = 0; j < NUM_COLS; ++j){
if(milesTracker[i][j] > maxMiles){
maxMiles = milesTracker[i][j];
}
}
}
for(i = 0; i < NUM_ROWS; ++i){
for(j = 0; j < NUM_COLS; ++j){
if(milesTracker[i][j] < minMiles){
minMiles = milesTracker[i][j];
}
}
}
//edit to here
System.out.println("Min miles: " + minMiles);
System.out.println("Max miles: " + maxMiles);
}
Answers
Answer: 40, 4
Explanation:
Data Structure in C++
Using namespace std;
In this assignment you will implement a variation of Mergesort known as a bitonic mergesort, recursively.
In a normal mergesort, the input to the merge step is a single array, which is divided into two sections, both sorted ascending. We assume that the first half (0 up to but not including size/2) is the first section and the second half (size/2 up to but not including size) is the second section.
In a bitonic mergesort, we use the same arrangement, except that the second sequence is sorted in descending order: the first half goes up, and then the second half goes down. This means that when we are doing a merge, sometimes we want to merge the results into ascending order, while other times we want to merge into descending order (depending on which "half" of the final array the result will end up in). So we add another parameter, to describe the direction the output should be sorted into:
void merge(int* input, int size, int* output, bool output_asc);
If output_asc == true then after the merge output should contain size elements, sorted in ascending order. If output_asc == false, output should contain the elements sorted in descending order.
The other thing we glossed over in class was the allocation of the temporary space needed by the algorithm. It’s quite wasteful to allocate it in each recursive call: it would be better to allocate all the necessary space up front, and then just pass a pointer to it. In order to do this, we’ll write the recursive mergesort function in a helper function which will preallocate the space needed for the results:
int* mergesort(int* input, int size) {
int* output = new int[size];
mergesort(input, size, output, true);
return output;
}
void mergesort(int *input, int size, int* output, bool output_asc) {
// Your implementation here
}
The parameter output_asc serves the same purpose here as for merge: it tells the function that we want the output to be sorted ascending.
Interface
You must implement the functions
void merge(int* input, int size, int* output, bool output_asc);
int* mergesort(int* input, int size);
void mergesort(int *input, int size, int* output, bool output_asc);
Download a template .cpp file containing these definitions. This file is also available on the server in /usr/local/class/src.
merge must run in O(n) time with n= size. mergesort (both versions) must run in O(nlogn) time, and must use O(n) space. If you allocate any space other than the output array, you should free it before your function returns.
The test runner will test each function separately, and then in combination. It checks the result of sorting to make sure that it’s actually sorted, and then nothing is missing or added from the original (unsorted) sequence.
Answers
The code .cpp is available bellow
#include<iostream>
using namespace std;
//declaring variables
void merge(int* ip, int sz, int* opt, bool opt_asc); //merging
int* mergesort(int* ip, int sz);
void mergesort(int *ip, int sz, int* opt, bool opt_asc);
void merge(int* ip, int sz, int* opt, bool opt_asc)
{
int s1 = 0;
int mid_sz = sz / 2;
int s2 = mid_sz;
int e2 = sz;
int s3 = 0;
int end3 = sz;
int i, j;
if (opt_asc==true)
{
i = s1;
j = e2 - 1;
while (i < mid_sz && j >= s2)
{
if (*(ip + i) > *(ip + j))
{
*(opt + s3) = *(ip + j);
s3++;
j--;
}
else if (*(ip + i) <= *(ip + j))
{
*(opt + s3) = *(ip + i);
s3++;
i++;
}
}
if (i != mid_sz)
{
while (i < mid_sz)
{
*(opt + s3) = *(ip + i);
s3++;
i++;
}
}
if (j >= s2)
{
while (j >= s2)
{
*(opt + s3) = *(ip + j);
s3++;
j--;
}
}
}
else
{
i = mid_sz - 1;
j = s2;
while (i >= s1 && j <e2)
{
if (*(ip + i) > *(ip + j))
{
*(opt + s3) = *(ip + i);
s3++;
i--;
}
else if (*(ip + i) <= *(ip + j))
{
*(opt + s3) = *(ip + j);
s3++;
j++;
}
}
if (i >= s1)
{
while (i >= s1)
{
*(opt + s3) = *(ip + i);
s3++;
i--;
}
}
if (j != e2)
{
while (j < e2)
{
*(opt + s3) = *(ip + j);
s3++;
j++;
}
}
}
for (i = 0; i < sz; i++)
*(ip + i) = *(opt + i);
}
int* mergesort(int* ip, int sz)
{
int* opt = new int[sz];
mergesort(ip, sz, opt, true);
return opt;
}
void mergesort(int *ip, int sz, int* opt, bool opt_asc)
{
if (sz > 1)
{
int q = sz / 2;
mergesort(ip, sz / 2, opt, true);
mergesort(ip + sz / 2, sz - sz / 2, opt + sz / 2, false);
merge(ip, sz, opt, opt_asc);
}
}
int main()
{
int arr1[12] = { 5, 6, 9, 8,25,36, 3, 2, 5, 16, 87, 12 };
int arr2[14] = { 2, 3, 4, 5, 1, 20,15,30, 2, 3, 4, 6, 9,12 };
int arr3[10] = { 10, 9, 8, 7, 6, 5, 4, 3, 2, 1 };
int *opt;
cout << "Arays after sorting:\n";
cout << "Array 1 : ";
opt = mergesort(arr1, 12);
for (int i = 0; i < 12; i++)
cout << opt[i] << " ";
cout << endl;
cout << "Array 2 : ";
opt = mergesort(arr2, 14);
for (int i = 0; i < 14; i++)
cout << opt[i] << " ";
cout << endl;
cout << "Array 3 : ";
opt = mergesort(arr3, 10);
for (int i = 0; i < 10; i++)
cout << opt[i] << " ";
cout << endl;
return 0;
}
Convert the following C program to C++.
More instructions follow the code.
#include
#include
#define SIZE 5
int main(int argc, char *argv[]) {
int numerator = 25;
int denominator = 10;
int i = 0;
/*
You can assume the files opened correctly and the
correct number of of command-line arguments were
entered.
*/
FILE * inPut = fopen(argv[1], "r");
FILE * outPut = fopen(argv[2], "w");
float result = (float)numerator/denominator;
fprintf(outPut,"Result is %.2f\n", result);
float arr[SIZE];
for( ; i < SIZE; i++) {
fscanf(inPut, "%f", &arr[i]);
fprintf(outPut, "%7.4f\n", arr[i]);
}
return 0;
}
Notice this is uses command-line arguments. I have provided an input file called num.txt that will be used when running the program. The output file is called out.txt.
Make sure you are using C++ style file I/O (FILE pointers/fopen) as well as regular I/O including the C++ style output formatting (fscanf, fprintf, formatting). Also use the C++ method of casting. The lines above that are bold are the lines that you need to convert to C++. Don't forget to add the necessary C++ statements that precede the main() function.
Answers
Answer:
The program equivalent in C++ is:
#include <cstdio>
#include <cstdlib>
#define SIZE 5
using namespace std;
int main(int argc, char *argv[]) {
int numerator = 25;
int denominator = 10;
FILE * inPut = fopen(argv[1], "r");
FILE * outPut = fopen(argv[2], "w");
float result = (float)numerator/denominator;
fprintf(outPut,"Result is %.2f\n", result);
float arr[SIZE];
for(int i = 0; i < SIZE; i++) {
fscanf(inPut, "%f", &arr[i]);
fprintf(outPut, "%7.4f\n", arr[i]);
}
return 0;
}
Explanation:
See attachment for explanation.
Each line were numbered with equivalent line number in the C program
Given four values representing counts of quarters, dimes, nickels and pennies, output the total amount as dollars and cents. Output each floating-point value with two digits after the decimal point, which can be achieved as follows: System.out.printf("Amount: $%.2f\n", dollars); Ex: If the input is: 4 3 2 1 where 4 is the number of quarters, 3 is the number of dimes, 2 is the number of nickels, and 1 is the number of pennies, the output is: Amount: $1.41 For simplicity, assume input is non-negative.
LAB ACTIVITY 2.32.1: LAB: Convert to dollars 0/10 LabProgram.java Load default template. 1 import java.util.Scanner; 2 3 public class LabProgram 4 public static void main(String[] args) { 5 Scanner scnr = new Scanner(System.in); 6 7 /* Type your code here. */|| 8 9) Develop mode Submit mode Run your program as often as you'd like, before submitting for grading. Below, type any needed input values in the first box, then click Run program and observe the program's output in the second box Enter program input (optional) If your code requires input values, provide them here. Run program Input (from above) 1 LabProgram.java (Your program) Output (shown below) Program output displayed here
Answers
Answer:
The corrected program is:
import java.util.Scanner;
public class LabProgram{
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int qtr, dime, nickel, penny;
double dollars;
System.out.print("Quarters: ");
qtr =scnr.nextInt();
System.out.print("Dimes: ");
dime = scnr.nextInt();
System.out.print("Nickel: ");
nickel = scnr.nextInt();
System.out.print("Penny: ");
penny = scnr.nextInt();
dollars = qtr * 0.25 + dime * 0.1 + nickel * 0.05 + penny * 0.01;
System.out.printf("Amount: $%.2f\n", dollars);
System.out.print((dollars * 100)+" cents");
}
}
Explanation:
I've added the full program as an attachment where I used comments as explanation
5-5. Design an Ethernet network to connect a single client P C to a single server. Both the client and the server will connect to their workgroup switches via U T P. The two devices are 900 meters apart. They need to communicate at 800 M b p s. Your design will specify the locations of any switches and the transmission link between the switches.
5-6. Add to your design in the previous question. Add another client next to the first client. Both connect to the same switch. This second client will also communicate with the server and will also need 800 M b p s in transmission speed. Again, your design will specify the locations of switches and the transmission link between the switches.
Answers
Answer:
ok so u have take the 5 and put 6
Explanation:
5-5. Ethernet network design: UTP connections from client PC and server to workgroup switches, 900m fiber optic link between switches, 800 Mbps communication.
5-6. Additional client connects to the same switch, UTP connection, maintains existing fiber optic link, 800 Mbps communication with the server.
What is the explanation for this?5-5. For connecting a single client PC to a single server, both located 900 meters apart and requiring communication at 800 Mbps, the following Ethernet network design can be implemented:
- Client PC and server connect to their respective workgroup switches via UTP.
- Use fiber optic cables for the 900-meter transmission link between the switches.
- Install switches at the client PC and server locations.
- Ensure that the switches support at least 1 Gbps Ethernet speeds to accommodate the required transmission speed.
5-6. In addition to the previous design, for adding another client next to the first client:
- Connect both clients to the same switch.
- Use UTP cables to connect the second client to the switch.
- Ensure the switch supports 1 Gbps Ethernet speeds.
- Maintain the existing fiber optic transmission link between the switches.
- The second client can also communicate with the server at the required 800 Mbps transmission speed.
Learn more about Network Design at:
https://brainly.com/question/7181203
#SPJ2
If you want Nud3s add me on sc Kermit4lyfe1
Answers
Answer:
que pinga this is a hw website not snap
Explanation:
Consider a Stop-and-Wait protocol. Assume constant delays for all transmissions and the same delay for packets sent and ACKs sent. Assume no errors occur during transmission.
(a) Suppose that the timeout value is set to 1/2 of what is required to receive an acknowledgement, from the time a packet is sent. Give the complete sequence of frame exchanges when the sender has 3 frames to send to the receiver.
(b) Suppose that the timeout value is sent to 2 times the round trip time. Give the sequence of frame exchanges when 3 frames are sent but the first frame is lost.
Answers
Explanation:
question a) answer:
At the moment when it sends the package, then it has a waiting time for the acknowledgement from the receiver, however, the time will be split in two when the frameset size becomes two, meaning that two packages have been sent together, causing the receiver to acknowledge only one package.
question b) answer:
The timeout is equal to two times.
In cases when the frame size is 3, the frame will be lost since the timeout turns to be 2 times. Because the sender has to wait for the acknowledgement, therefore it will send other of the parcels.
Jax needs to write a block of code that will organize a list of items alphabetically. Which function should he use? append() print() sort() order()
Answers
In python, the sort() function will alphabetically sort a list of strings
To write a block of code that will organize a list of items alphabetically In python, the sort() function will alphabetically sort a list of strings.
What is python?A high-level, all-purpose programming language is Python. Code readability is prioritized in its design philosophy, which makes heavy use of indentation. Python uses garbage collection and has dynamic typing. It supports a variety of paradigms for programming, including functional, object-oriented, and structured programming.
Python is a popular computer programming language used to create software and websites, automate processes, and analyze data. Python is a general-purpose language, which means it may be used to make many various types of applications and isn't tailored for any particular issues.
Sorting in Python simply means putting the data in a specific format or order. The order of the data pieces can be sorted either ascendingly or descendingly. Python programming contains certain built-in functions that allow you to sort the list's elements, just like C++ and Java.
Therefore, Thus option (C) is correct.
Learn more about python here:
https://brainly.com/question/18502436
#SPJ2
Jason works as a financial investment advisor. He collects financial data from clients, processes the data online to calculate the risks associated with future investment decisions, and offers his clients real-time information immediately. Which type of data processing is Jason following in the transaction processing system?
A.
online decision support system
B.
online transaction processing
C.
online office support processing
D.
online batch processing
E.
online executive processing
Answers
I believe the answer is A. because he has to listen to what the people tell him and he information he has to think about and make a choice on what to reply with.
I hope this helps and its correct please let me know if its wrong have a great day//night.
sum_even Write a program that reads an integer 0 < n < 2^32, returns the sum of all digits in n that are divisible by 2. For example, if n = 341238 the output would be 14, because it is the sum of 4 + 2 + 8. Hint: a signed int may not be enough.
Answers
Answer:
Written in Python
n = int(input("Num: "))
sum_even = 0
if n > 0 and n < 2**32:
strn = str(n)
for i in range(0,len(strn)):
if int(strn[i])%2 == 0:
sum_even = sum_even+ int(strn[i])
print(sum_even)
Explanation:
This line prompt user for input
n = int(input("Num: "))
This line initializes sum_even to 0
sum_even = 0
This line checks for valid input
if n > 0 and n < 2**32:
This line converts input to string
strn = str(n)
This line iterates through each digit of the input
for i in range(0,len(strn)):
This if condition checks for even number
if int(strn[i])%2 == 0:
This adds the even numbers
sum_even = sum_even+ int(strn[i])
This prints the sum of all even number in the user input
print(sum_even)
Screenshot is the image of your active MS Word PowerPoint window
Is it true or false?
Answers
true
Screenshots are basically snapshots of your computer screen. You can take a screenshot of almost any program, website, or open window. PowerPoint makes it easy to insert a screenshot of an entire window or a screen clipping of part of a window in your presentation.
Using Phyton
Write a program with the following functions.
function 1: Accepts 2 strings as arguments. returns true if the second string is a part of the first string.
Answers
def something(string1, string2):
return True if string2 in string1 else False
This would be the most concise way of writing this function.
If Maya wants to access a view that would control multiple slides within a presentation, which view should she utilize? Master view Color view Slide Sorter view Normal view
Answers
Answer:
Slide Shorter View
Explanation:
If Maya wants to access a view that would control multiple slides within a presentation, which view should she utilize Slide Shorter View.
What is Slide shorter view?View of the Slide Sorter from the task bar displays the Slide View button in PowerPoint, either from the View tab on the ribbon or at the bottom of the slide window.
The Slide Sorter view (below) shows thumbnails of each slide in your presentation in a horizontally stacked order. If you need to rearrange your slides, the slide show view comes in handy.
You can simply click and drag your slides to a new spot or add sections to categorize your slides into useful groupings.
Therefore, If Maya wants to access a view that would control multiple slides within a presentation, which view should she utilize Slide Shorter View.
To learn more about Slide shorter view, refer to the link:
https://brainly.com/question/13736919
#SPJ6
A ______________ is a way of taking a screenshot or a picture of your computer screen.
Answers
Answer:
prt scan+Windows logo
Why the shape of a cell is hexagonal
Answers
Answer:
Hexagonal cell shape is perfect over square or triangular cell shapes in cellular architecture because it cover an entire area without overlapping i.e. they can cover the entire geographical region without any gaps.
I hope this helps
Pls mark as brainliest
Plz answer me will mark as brainliest
Answers
Answer:
7. true
8.B
Hopefully those are correct!
Explanation:
Backing up and synchronization are the same thing.
A.)True
B.) False
Answers
Answer: A.)true
Explanation: This is true for a number of reasons, the first being that synced files
You have been given two classes, a Main.java and a Coin.java. The coin class represents a coin. Any object made from it will have a 1) name, 2) weight and 3) value. As of now, the instance variables in Coin.java are all public, and the main function is calling these variables directly for the one coin made in it.
Required:
Your goal is to enforce information hiding principles in this tasl. Take Coin.java, make all instance variables private and create set/get functions for each instance variable. Then replace the direct references in main() to each instance variable with a call to an appropriate set or get function.
Answers
Answer:
Here is the Coin class:
public class Coin { //class names
private int value; // private member variable of type int of class Coin to store the value
private String coinName; // private member variable of type String of class Coin to store the coint name
private double weight; //private member variable of type double of class Coin to store the weight
public void setValue (int v) { //mutator method to set the value field
value = v; }
public void setName(String n){ //mutator method to set coinName field
coinName = n;}
public void setWeight (double w) { //mutator method to set weight field
weight = w; }
public int getValue () { //accessor method to get the value
return value; } // returns the current value
public String getName () { //accessor method to get the coin name
return coinName; } //returns the current coin name
public double getWeight () { //accessor method to get the weight
return weight; } } //returns the current weight
Explanation:
Here is the Main.java
public class Main{ //class name
public static void main(String[] args) { //start of main method
Coin penny = new Coin(); //creates object of Coin class called penny
penny.setName("Penny"); //calls setName method of Coin using object penny to set the coinName to Penny
penny.setValue(1); //calls setValue method of Coin using object penny to set the coin value to 1
penny.setWeight(0.003); //calls setWeight method of Coin using object penny to set the coin weight to 0.003
System.out.println("Coin name: " + penny.getName()); // calls getName method of Coin using penny object to get the current coin name stored in coinName field
System.out.println("Coin value: " + penny.getValue()); // calls getValue method of Coin using penny object to get the coin value stored in value field
System.out.println("Coin weight: " +penny.getWeight()); }} // calls getWeight method of Coin using penny object to get the coin weight stored in weight field
The value of coinName is set to Penny, that of value is set to 1 and that of weight is set to 0.003 using mutator method and then the accessor methods to access these values and prinln() to display these accessed values on output screen. Hence the output of the entire program is:
Coin name: Penny Coin value: 1 Coin weight: 0.003
The screenshot of the program along with its output is attached.
What is the process to add images to your library panel in Adobe Animate CC?
Answer choices
Choose file>import>import library
Choose file>open>insert image
Choose file>export>export file
Choose file> New> file
Answers
Answer:
Choose file>import>import library
Explanation:
because it is the process to add images to your library
Which of the following is a feature of high-level code?
Language makes it easier to detect problems
Requires a lot of experience
Easy for a computer to understand
Runs quicker